
Future-Proofing Your Privacy: The Next Generation of Cryptography

Future-Proofing Your Privacy: The Next Generation of Cryptography
Key Takeaways
- Harvest Now, Decrypt Later attacks involve storing encrypted data for the future, when the techology exists to decrypt it.
- Quantum computers pose a threat to current encryption schemes, but post-quantum cryptography aims to safeguard against this.
- Companies are implementing post-quantum encryption standards, like Apple’s PQ3, to secure data against future attacks and stay ahead of potential breaches.
Encryption keeps data safe, even when it falls into the wrong hands. But what happens in the future, when the available computational power renders current encryption methods obsolete? Is your personal data at risk? Let’s explore.
What’s a Harvest Now, Decrypt Later Attack?
A Harvest Now, Decrypt Later attack involves acquiring data in an encrypted state and storing it so that it can be decrypted in the future. Also known as retrospective decryption, this encrypted data is effectively archived until technology reaches a state where it can be decrypted and accessed.
The computers of today will never come close to cracking so-called gold standard 256-bit encryption schemes. To quote Bruce Schneier , author of Applied Cryptography: “brute-force attacks against 256-bit keys will be infeasible until computers are built from something other than matter and occupy something other than space.”
Encryption is what keeps your data safe, from payment details and login credentials to device backups and device connections to websites like this one. When data breaches occur, serious damage is done when it turns out that sensitive data is stored in an unencrypted state. It’s why the web switched to HTTPS , making it impossible for data captured in transit to be of use to bad actors.
When data breaches occur and the targets are quick to point out that payment details and login credentials are not affected, it’s usually thanks to the encryption methods used to keep this information safe.
Harvest Now, Decrypt Later is like stealing the whole safe, rather than just the contents of the safe, in the hope that you’ll eventually get the right tools to break it open. And those tools are coming, since the cryptographic algorithms we’ve come to rely on won’t be safe forever.
The Looming Threat of Quantum Computing
Though computer hardware continues to improve year-on-year, Moore’s Law is dead . This is the idea that transistor density doubles every two years, effectively doubling performance (or halving cost). We are now reaching the limits of how small these transistors can be. The speed of advances has slowed and, though there’s more to performance than how many transistors can fit on a single chip, so too has the pace of improvement.
This is why the next game-changing boost in computing power will come from quantum computers. Whereas existing computer technology stores information in bits that can take the form of 0 or 1, quantum computers can exist in a superposition of both 0 and 1 at the same time.
By harnessing the laws of quantum physics, quantum computers are able to solve far more complex problems than existing classical computers can and in less time. This includes being able to crack existing encryption algorithms, which is what makes retrospective decryption a very real threat. This is done using brute force attacks , where all possible solutions to current cryptography problems can be tested within a reasonable timeframe.
Today’s quantum computers are huge, require significant cooling, and are still susceptible to errors. Current predictions by consulting firms like McKinsey & Company suggest that we shouldn’t expect a stable quantum computer at scale until 2040 or later, though some predict it will be earlier.
How long it will be until the general public gets their hands on this sort of power remains to be seen, but what about industry and the state? Governments around the world are investing billions into quantum research, and it’s easy to see the strategic advantage of getting your hands on such a technology first. Nobody needs your smartphone passcode if they can just break the lock.
For now, it’s a waiting game. For existing data breaches, where encrypted volumes have already been captured and are secured with old algorithms, time is running out. But just as computers move forward, so too does cryptography. If the problem is too easy to solve, the solution is to make the problem harder.
How Are Companies Protecting Against Future Attacks?
Post-quantum cryptography hopes to safeguard encryption algorithms against the threats posed by quantum computers. The idea is to design cryptographic problems that are suitably difficult to solve, even with computers that are vastly more powerful than those we currently have access to.
The good news is that you don’t need quantum computers to design complex cryptographic problems. Governments and companies around the world are hard at work designing these problems and making them work with existing protocols like TLS, which is used to secure browsing sessions, email, and more.
In 2022, the US National Institute of Standards and Technology announced the winners of its competition to develop and standardize new post-quantum encryption algorithms. This resulted in a new set of cryptographic primitives that use different mathematical principles to those favored by the algorithms used in classical computing.
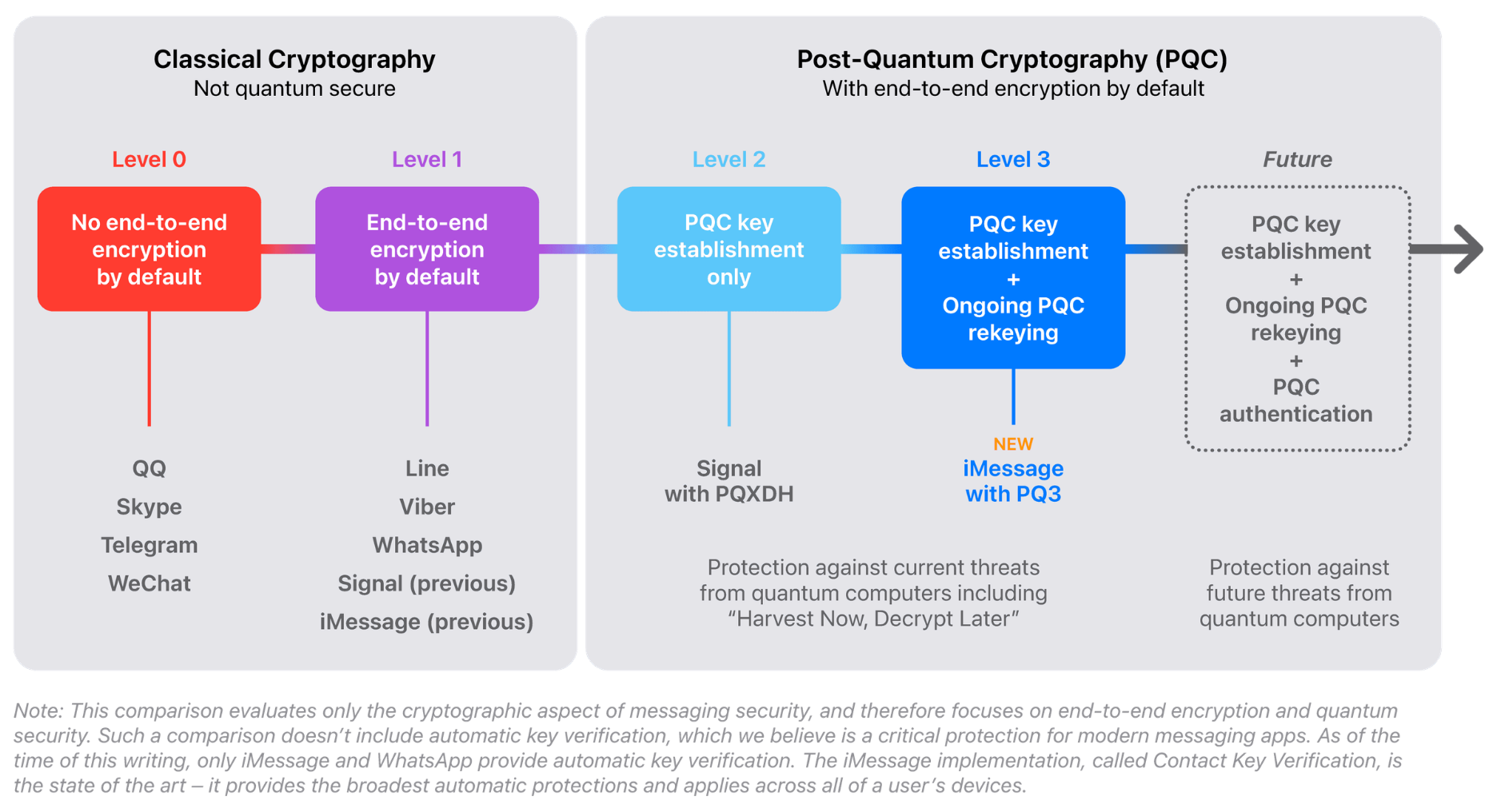
Post-quantum encryption is already making its way into consumer technology. Apple’s iOS 17.4 update for iPhone (as well as iPadOS 17.4, macOS 14.4, and watchOS 10.4) introduced PQ3, a post-quantum encryption standard with the aim of securing the iMessage protocol against future attacks.
In an Apple Security Research blog post, the company claims to have designed the first messaging protocol that reaches what it describes as Level 3 security, surpassing the PQXDH standard implemented by secure messaging app Signal in late 2023.
Apple
Companies like IBM already offer quantum-safe cryptographic testing for enterprise clients and even offer to shore up protection against future attacks. Governments around the world are among the first to start implementing these safeguards.
There’s a real incentive to put many more padlocks on the door than is necessary right now. The better we protect current data, the better it will be protected in the future.
Encryption Is An Ever-Evolving Technology
Like many aspects of technology, encryption is a game of cat and mouse. As computers become more powerful and capable, security must evolve to stay one step ahead. This will always be the case.
Expect to see more of your everyday services implement quantum-proof safeguards in the years to come. Just try not to worry too much about all the old encrypted data that’s already sitting on hard drives, as Q-Day marches ever closer.
Also read:
- [New] 2024 Approved What Hidden Beats Within Facebook Are You Overlooking?
- [Updated] 2024 Approved Quietude in a Click The Ultimate Calm List
- 2024 Approved Freeze-Frame Creation Through Stabilized Capture
- ChatGPT Unleashed: Eight Innovative Ways to Advance Your Business Operations
- Explore Apple's Innovative 3D Spatial Videos on Your Meta Quest 3: A Step-by-Step Guide
- How to Ask ChatGPT to Help Modify Your Car
- How to Remove an AirTag from Your Apple ID Account From Apple iPhone 11?
- How to Stream Apple iPhone SE (2020) to Computer? | Dr.fone
- In 2024, Filmora’s Recipe for Captivating YouTube Trailers
- In 2024, Set Your Preferred Job Location on LinkedIn App of your Oppo K11x | Dr.fone
- Mastering the Move: Top Secrets for Flawlessly Upgrading to Your New iPhone | ZDNet's How-To Guide
- Step-by-Step Guide: Removing a User Account From Windows 10 with Ease
- Uniting Users with Distinctive Chatbot Experiences
- Upcoming Release Date: Everything You Need to Know About the Latest AirPods - How & Where to Place Your Preorder
- Title: Future-Proofing Your Privacy: The Next Generation of Cryptography
- Author: Brian
- Created at : 2025-01-25 01:45:16
- Updated at : 2025-01-31 20:40:07
- Link: https://tech-savvy.techidaily.com/future-proofing-your-privacy-the-next-generation-of-cryptography/
- License: This work is licensed under CC BY-NC-SA 4.0.